Learn about data processing, model formulation, and hypothesis testing in this comprehensive analysis.
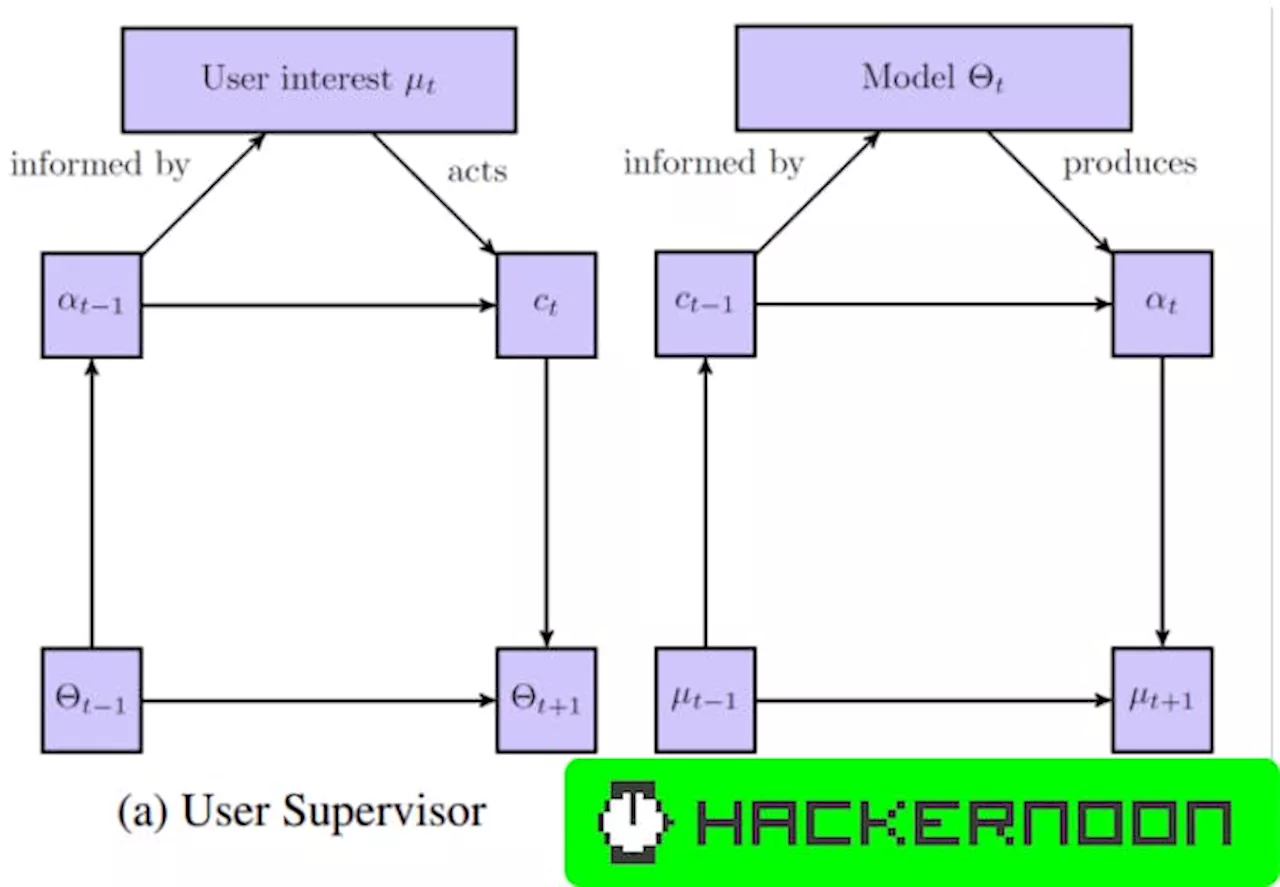
Authors: Jonathan H. Rystrøm. Table of Links Abstract and Introduction Previous Literature Methods and Data Results Discussions Conclusions and References A. Validation of Assumptions B. Other Models C. Pre-processing steps 3 Methods and Data 3.1 Defining Barrier-to-Exit On a high level, Barrier-to-Exit measures how much effort users must expend to signal that their preferences have changed .
Table of Links Abstract and Introduction Abstract and Introduction Previous Literature Previous Literature Methods and Data Methods and Data Results Results Discussions Discussions Conclusions and References Conclusions and References A. Validation of Assumptions A. Validation of Assumptions B. Other Models B. Other Models C. Pre-processing steps C. Pre-processing steps 3 Methods and Data 3.
United Kingdom Latest News, United Kingdom Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
 Westbound Interstate 70 closed near Eagle for crashThe road is closed between exit 157 and exit 147.
Westbound Interstate 70 closed near Eagle for crashThe road is closed between exit 157 and exit 147.
Read more »
 I-90 closes from Exit 63 to Exit 70 for emergency tree removalI-90 closed Friday afternoon for emergency tree removal, the Washington State of Transportation (WSDOT) reported Friday. The closure began at 1 p.m. and
I-90 closes from Exit 63 to Exit 70 for emergency tree removalI-90 closed Friday afternoon for emergency tree removal, the Washington State of Transportation (WSDOT) reported Friday. The closure began at 1 p.m. and
Read more »
 Amazon’s Ali Kole Talks the Multifaceted Amazon ShopperAfter signing Clinique, Amazon Premium Beauty outlines the various purchasing behaviors motivating its consumers.
Amazon’s Ali Kole Talks the Multifaceted Amazon ShopperAfter signing Clinique, Amazon Premium Beauty outlines the various purchasing behaviors motivating its consumers.
Read more »
 NATO marks its 75th birthday as Russia's war in Ukraine gnaws at its unityRetail giant Amazon will be laying off workers from its Amazon Web Services division
NATO marks its 75th birthday as Russia's war in Ukraine gnaws at its unityRetail giant Amazon will be laying off workers from its Amazon Web Services division
Read more »
 Understanding the Play-to-Earn Model of Gaming Emerging from CryptoCrypto online games (also known as blockchain games) are now more popular than ever, and both new technologies are helping to shape the future of the gaming and iGaming industries.
Understanding the Play-to-Earn Model of Gaming Emerging from CryptoCrypto online games (also known as blockchain games) are now more popular than ever, and both new technologies are helping to shape the future of the gaming and iGaming industries.
Read more »
 Understanding the Threat Model: Black-Box Attacks on Malware Detection SystemsExplore black-box attacks in the context of malware evasion, where attackers use limited information on target systems to modify malware and evade detection.
Understanding the Threat Model: Black-Box Attacks on Malware Detection SystemsExplore black-box attacks in the context of malware evasion, where attackers use limited information on target systems to modify malware and evade detection.
Read more »